
We’re massive fans of Cloudflare and deploy it as part of our speed optimization services.
Cloudflare has an amazing range of features and options and a lot of the features go unused or under leveraged. In this post we’ll share three Cloudflare that will both help improve the security or your WordPress site and at the same time also reduce the load on your site and help speed it up.
These are really easy to setup and if you’re moderately tech savvy will take you maybe 10-15 minutes. Click the images to enlarge.
Table of Contents
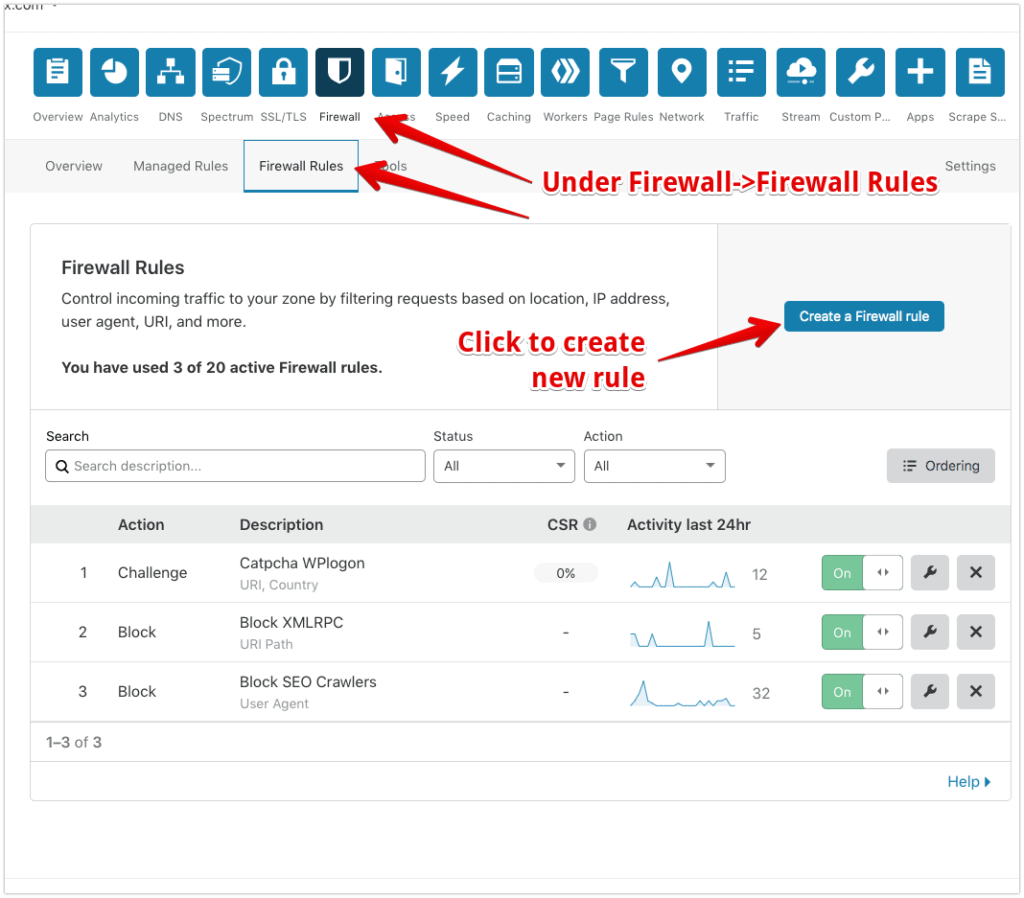
How to add Cloudflare Firewall rules
Firewall rules can be added under the Firewall menu->Firewall Rules tab in Cloudflare. The free plan gives you up to 5 rules so these can be added at no cost.
Once you add a rule it takes effect almost immediately.
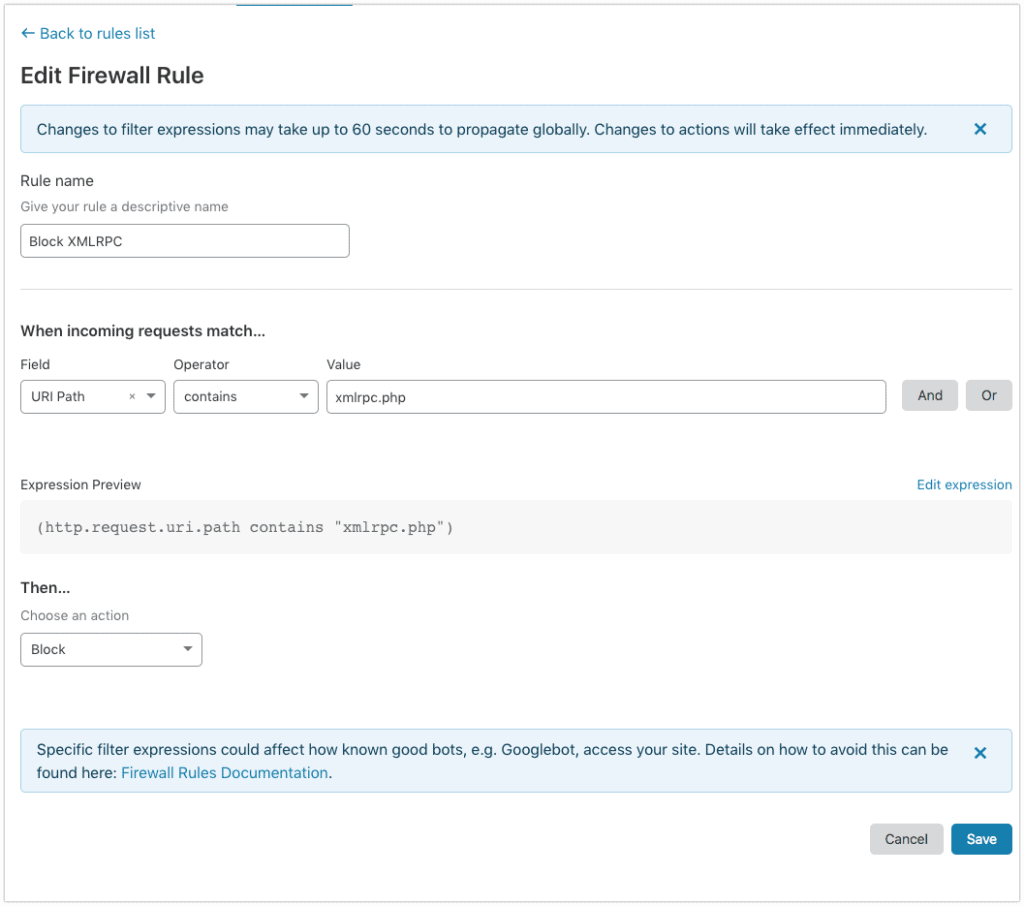
1. Block access to XMLRPC.php
This is an older WordPress API interface that is very rarely used but is a vector for many attacks.
Hammering this file with requests can very quickly chew up a lot of CPU cycles and on a shared host or host with low CPU or resources available it may start throwing 502 and 504 errors.
2. Block SEO Bots & Crawlers
With this rule we block traffic from Ahrefs, Semrush and Opensite explorer (SEO Moz bot) SEO bots.
These are extremely aggressive crawlers and particularly on Woocommerce they’ll rapidly add and remove things from the cart multiple times per second again chewing a lot of CPU resources.
In addition, allowing them to crawl the site will also divulge some SEO information that competitors using these SEO tools may find useful.

3. Show a captcha message on the WordPress logon page
The typical WordPress site we see can get anywhere from 1000-10000 brute force logon attempts a day.
Adding a rule to show a captcha message to visitors hitting this page OR visitors hitting this page outside the home country of the site can dramatically reduce brute force password attempts and reduce a lot of load on the hosting.

Related Posts & Resources
SiteSpeedBot Website Speed Test Tool